Advent Of Cyber 3 - Day 3
tl;dr:
Content discovery
Today we get to attack a box and experiment with content discovery.
The address of the server is on tryhackme.com’s network so first we need to connect the attacking box via VPN to that network.
target IP: 10.10.73.115
If surfing to the IP address, a neat webpage is shown where you can register a user and browse around.
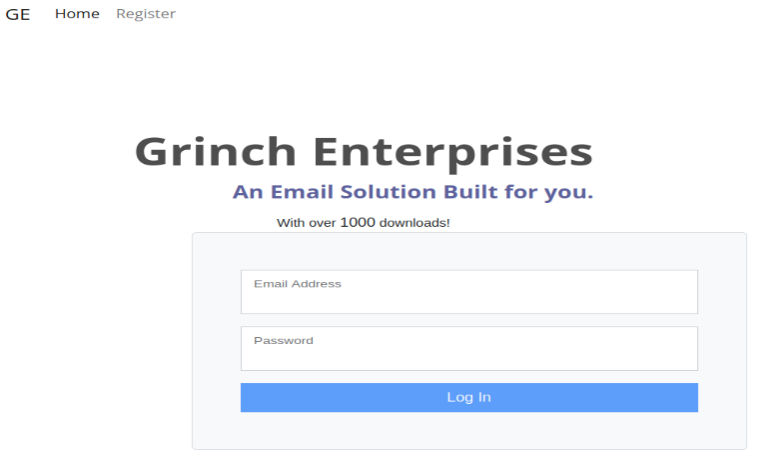
But we’re more interested in finding other juicy treats.
$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 40 -u http://10.10.73.115/
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.73.115/
[+] Method: GET
[+] Threads: 40
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/12/03 10:51:36 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 312] [--> http://10.10.73.115/admin/]
/assets (Status: 301) [Size: 313] [--> http://10.10.73.115/assets/]
/javascript (Status: 301) [Size: 317] [--> http://10.10.73.115/javascript/]
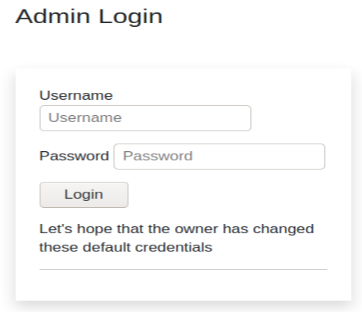
that /admin portal sure looks inviting.
the default user and password isn’t changed so we can log in with: user: administrator password: administrator
once logged in, the flag is shown: THM{ADM1N_AC3SS}
good rooms on tryhackme for learning more:
name of the discovered admin dashboard: admin (the /admin folder) password we found: administrator